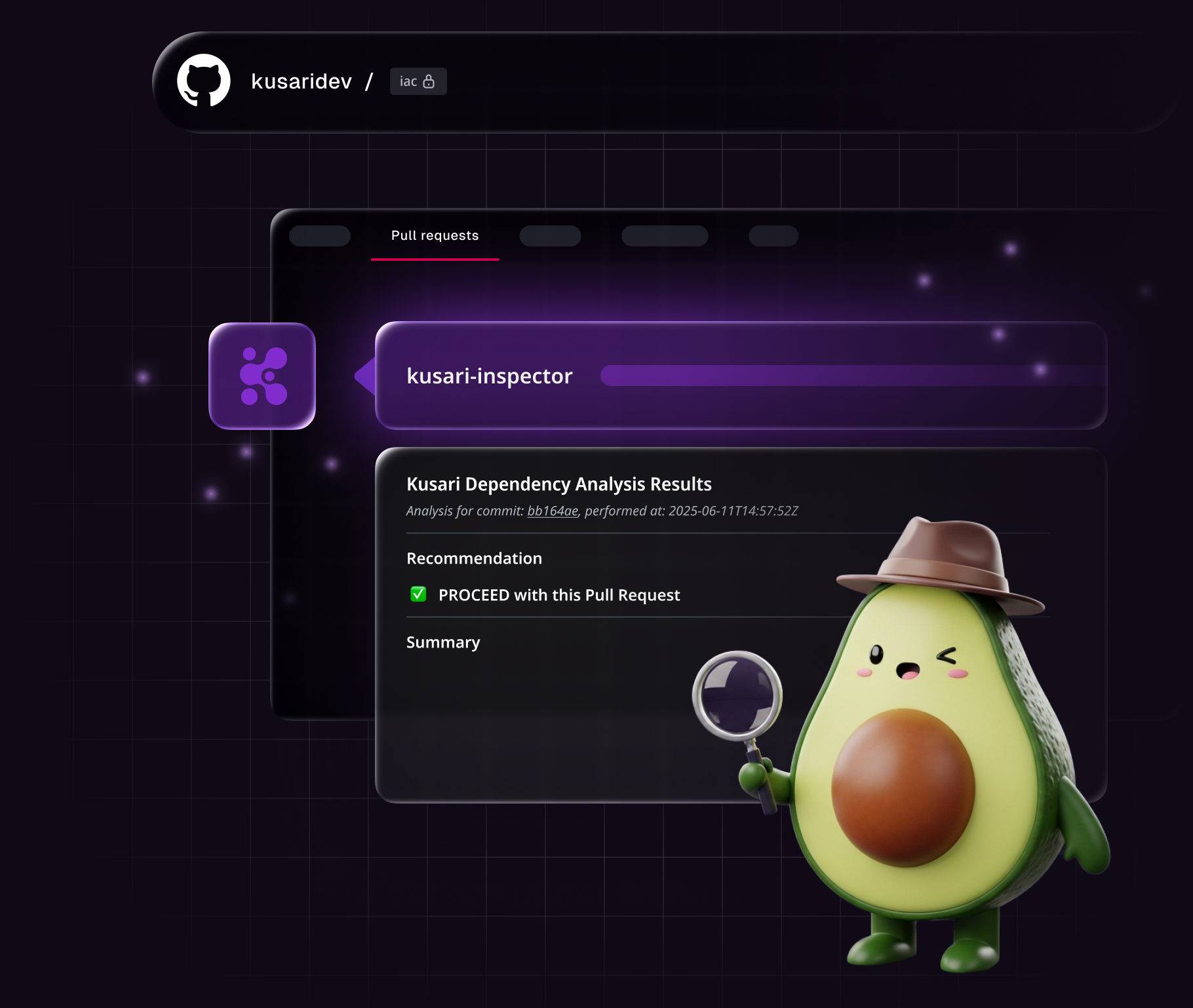
Kusari Inspector
Make developers your first line of defense
Help your developers choose secure components right in the tools they’re already using. You set the guardrails, they avoid unnecessary rework.
Trusted by developers and security teams
Your code stays in your repos—we never store it.
Deploy faster with security from the start
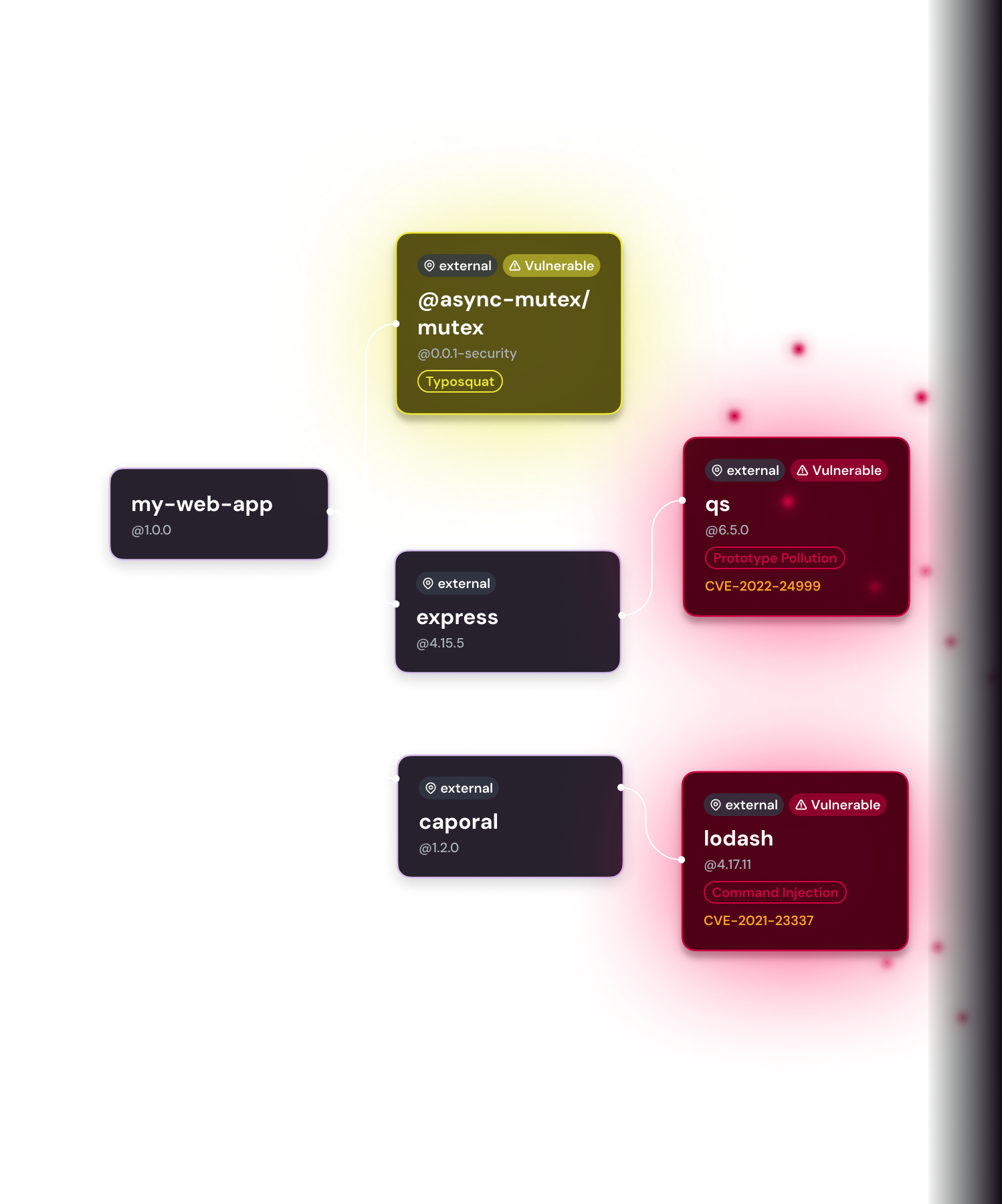
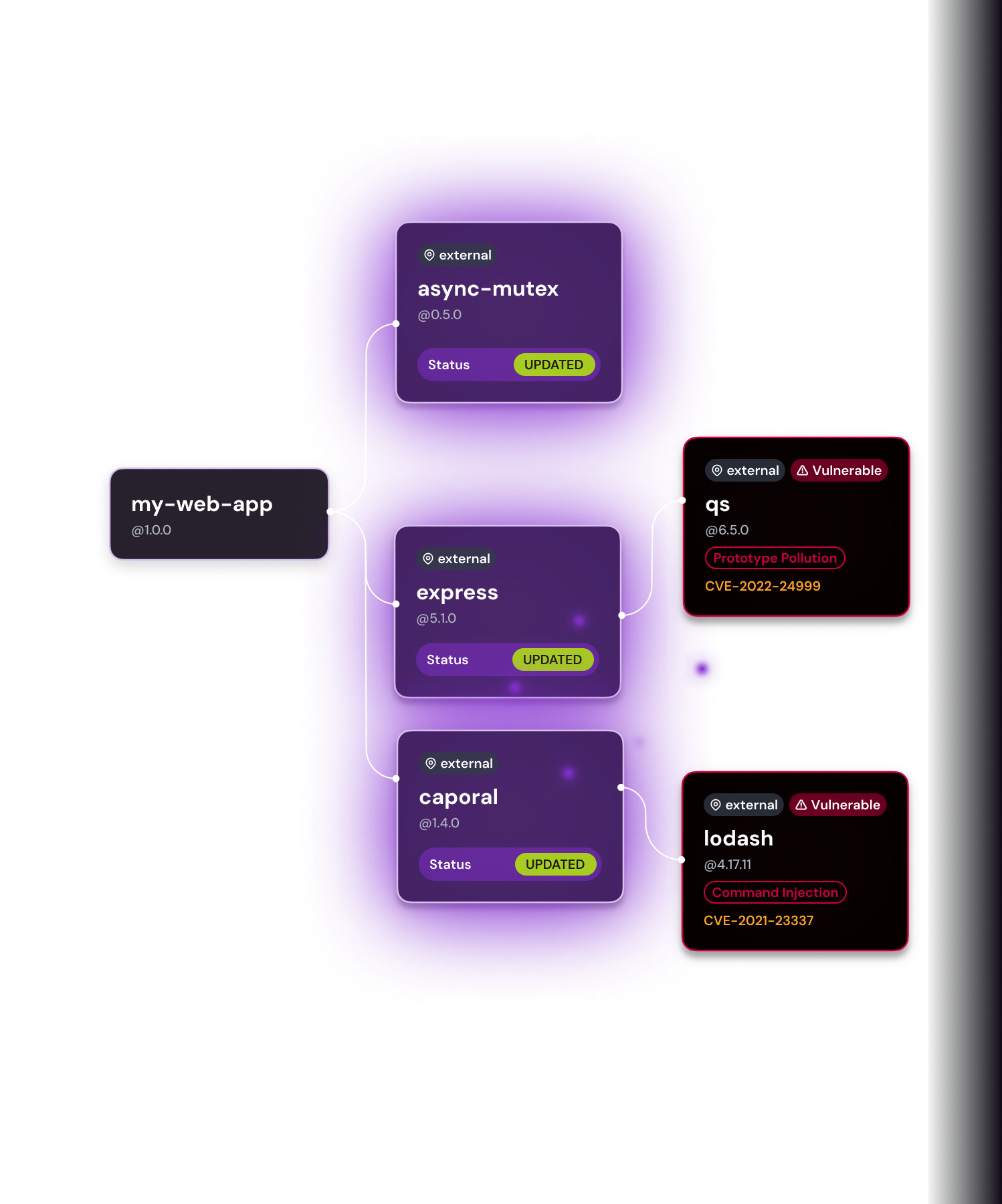
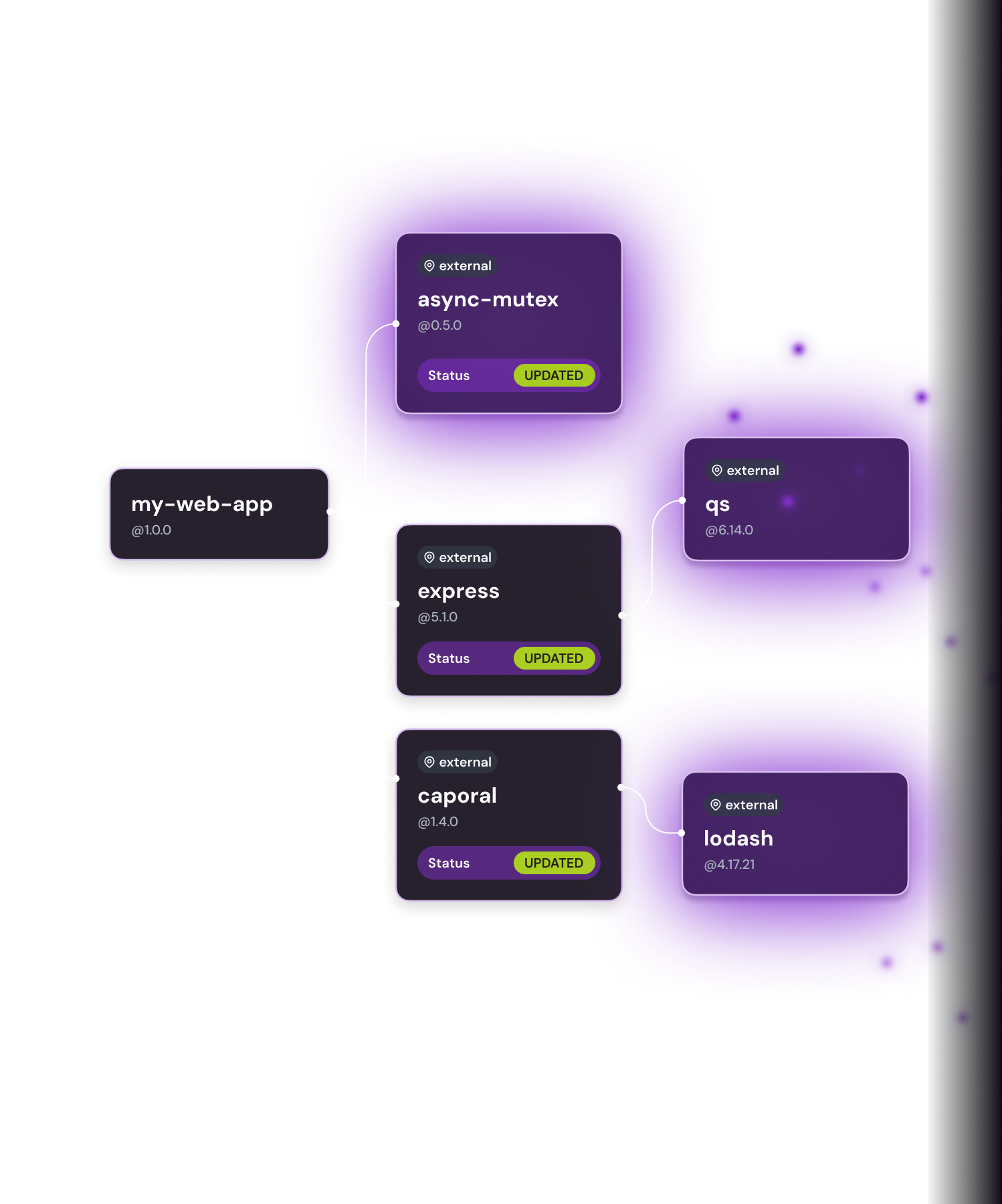
TRANSITIVE DEPENDENCY ANALYSIS
Fix it once and fix it right
You’re only as secure as the deepest dependency. Get remediation instructions that analyze the security of dependencies within each component as you go. Ensure every fix is reviewed across trusted signals like CVSS (for severity), EPSS (for exploitability) and exploited vulnerabilities in the VEX.
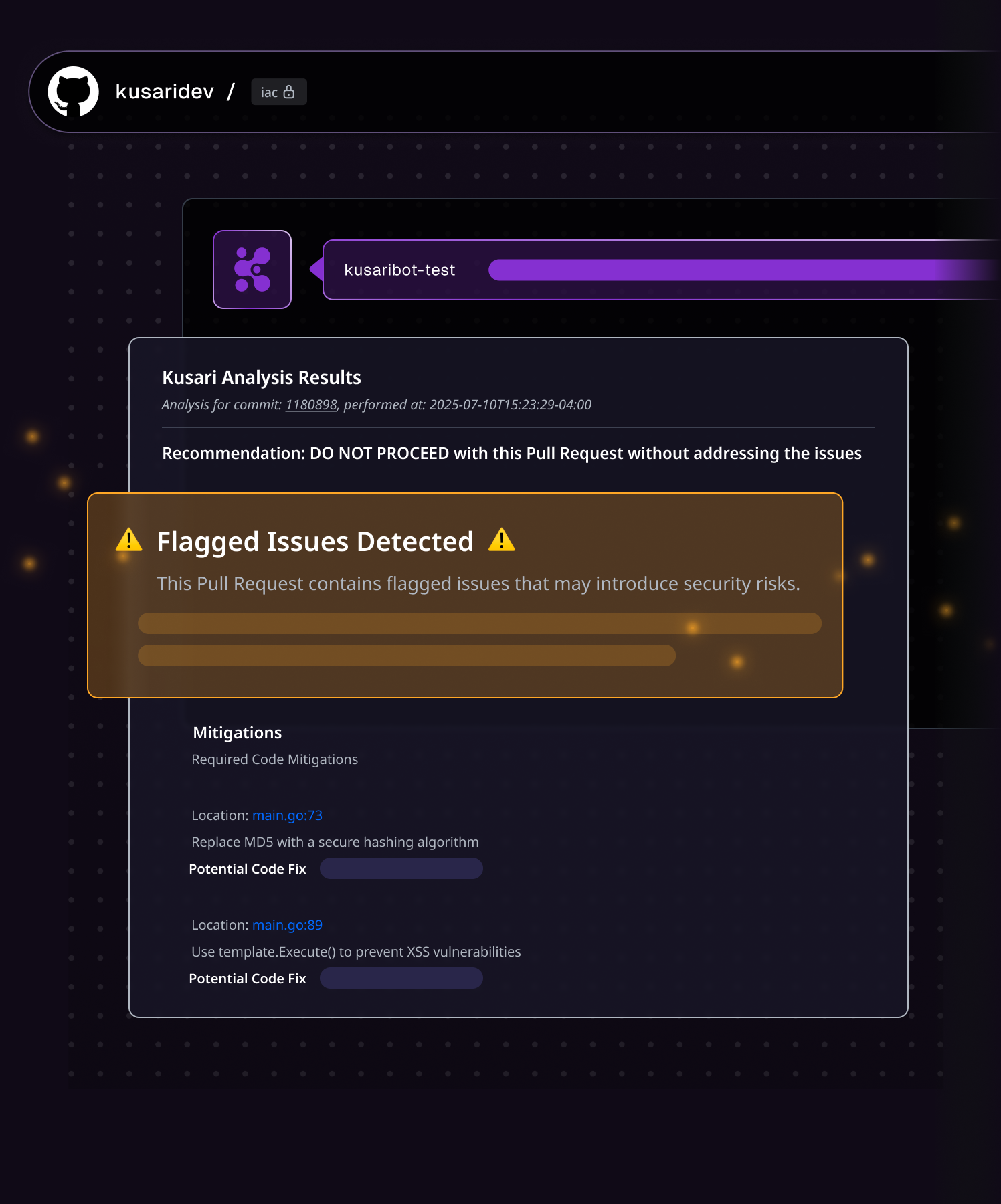
CODE SECURITY ANALYSIS
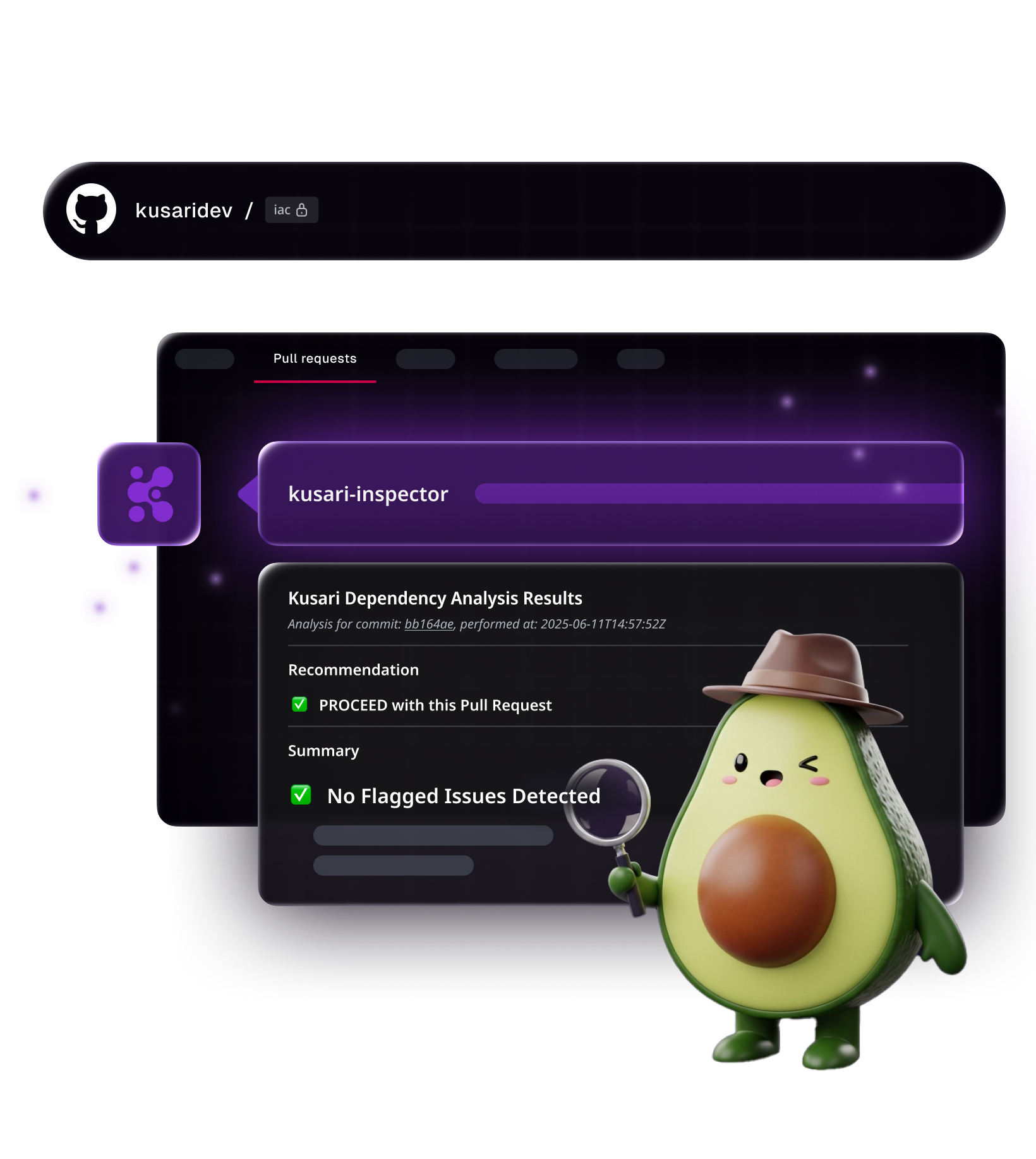
Check code right in your project
Security shouldn’t slow things down. Kusari Inspector helps you fix issues on the spot—with inline feedback, contextual remediation, and safe-to-merge recommendations in seconds. Automatically analyze your code for risky changes, suspicious diffs, and package-level threats in your software supply chain.











Works with your security tools
Use Inspector on its own or in combination with existing software supply chain security tools.

Kusari Platform
Integrate perfectly with the Kusari Platform to provide organization-wide insights into your open source software supply chain management.
Explore the full platform